Creating an AWS Hardware VPN Connection with Ubiquiti EdgeRouterX
 When you’re working with Amazon and vRealize Automation Software Components, one of the requirements is for the Guest Agent (gugent) to talk back to the vRealize Automation APIs - the gugent polls the API for tasks it should perform, downloads them from the API and executes them, then updates the tasks with a status.
When you’re working with Amazon and vRealize Automation Software Components, one of the requirements is for the Guest Agent (gugent) to talk back to the vRealize Automation APIs - the gugent polls the API for tasks it should perform, downloads them from the API and executes them, then updates the tasks with a status.
This means that Virtual Machines deployed as EC2 instances in an AWS VPC require the ability to talk back to internal corporate networks - not something you’d want to publish on the internet! That’s where AWS’s VPN connections come in - you can create several types of VPN that allow such communication over a secure (encrypted) virtual private network.
For the purposes of this post, I’m going to look at setting up the “AWS Hardware VPN”, which is described by Amazon:
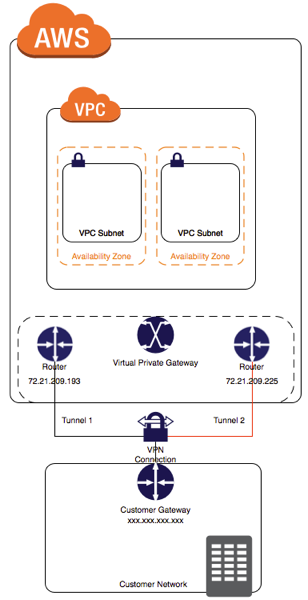
You can create an IPsec, hardware VPN connection between your VPC and your remote network. On the AWS side of the VPN connection, a virtual private gateway provides two VPN endpoints for automatic failover. You configure your customer gateway, which is the physical device or software application on the remote side of the VPN connection.
As with all things AWS, you have to create two of anything in different Availability Zones to call it Highly Available, or for any kind of SLA to apply. The VPN is no different, and as you can see from the diagram above you create two tunnels to provide a Highly Available connection to AWS.
To get a bit of a background on my AWS setup for vRealize Automation, take a look at this post - Adding an AWS endpoint to vRealize Automation 7. The VPCs and configuration described in this article are my starting point.
For my hardware VPN I am running a Ubiquiti EdgeRouterX, which is a fantastic little router, highly recommended. It has a tiny form factor, runs on Vyatta OS and even provides a PoE port for my Ubiquiti Unifi AP AC Lite.
Enough theory for now, lets configure a Customer Gateway!
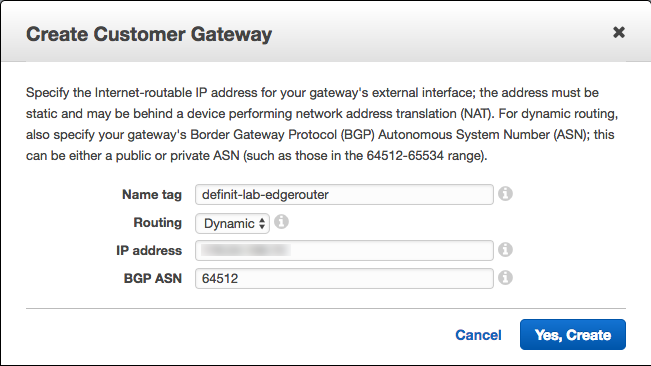
Create a Customer Gateway
A customer gateway defines your VPN endpoint from AWS’s point of view. Create a new one from the VPC Management console
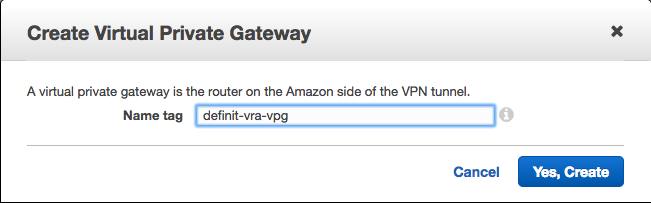
Create a Virtual Private Gateway
A Virtual Private Gateway is needed to provide a VPN concentrator on the Amazon side of things. It must be attached to the VPC you’re using for AWS in vRealize Automation.
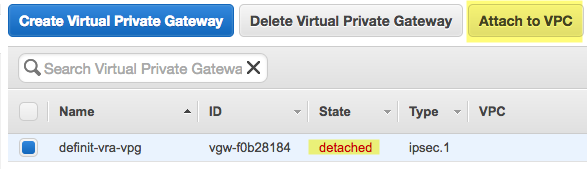
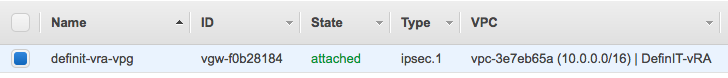
Now we can see the VPG is attached to the DefinIT-vRA VPC
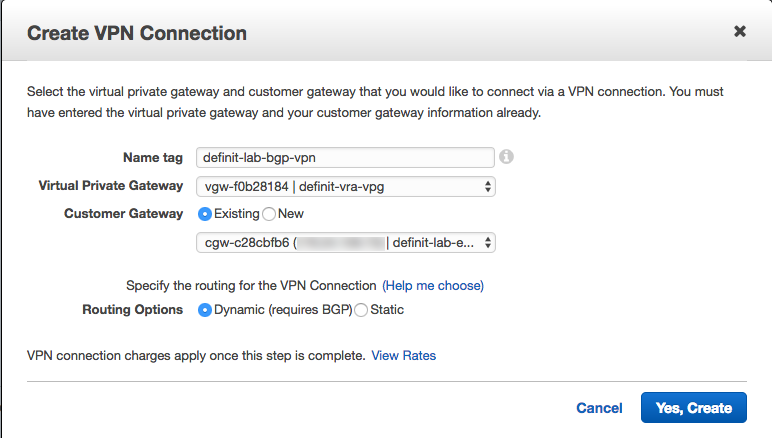
Create a VPN Connection
Now we have the components configured, we can link it together with a VPN connection. Note that once you complete the connection configuration your VPN charges apply.
Select the VPG and Customer Gateway we just configured, ensure you select Dynamic routing and give it a good name.
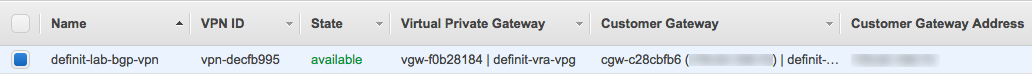
Creating the VPN connection took a couple of minutes to deploy - wait until you see the “available” state
Download the VPN Configuration
Since the EdgeRouter range are based on Vyatta, we can download the VPN configuration for Vyatta gateways. Hit the “Download Configuration” button and select Vyatta:
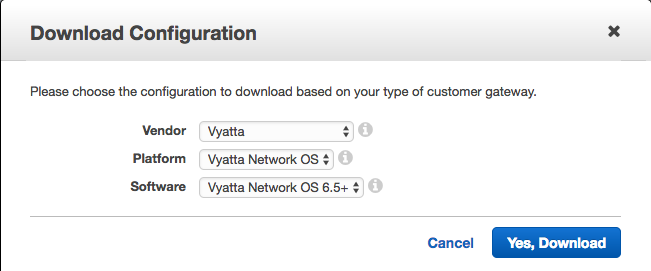 :
:
By default the configuration file will include a line to advertise 0.0.0.0/0 via BGP, which isn’t really desirable. Modify BOTH instances of this line:
set protocols bgp 64512 network 0.0.0.0/0
And added the network that I want to advertise:
set protocols bgp 64512 network 192.168.1.0/24
This subnet (192.168.1.0/24) is the subnet I have my vRA infrastructure on - the deployed VMs need to talk back to the vRA infrastructure to do my Application Components. If you want to advertise multiple subnets, simply duplicate this line and change the subnet.
Configuring the EdgeRouter
Firstly, take a backup of your configuration in case you need to roll back.
SSH to your EdgeRouter, enter configuration more (type configure) and paste in the modified configuration script from AWS:
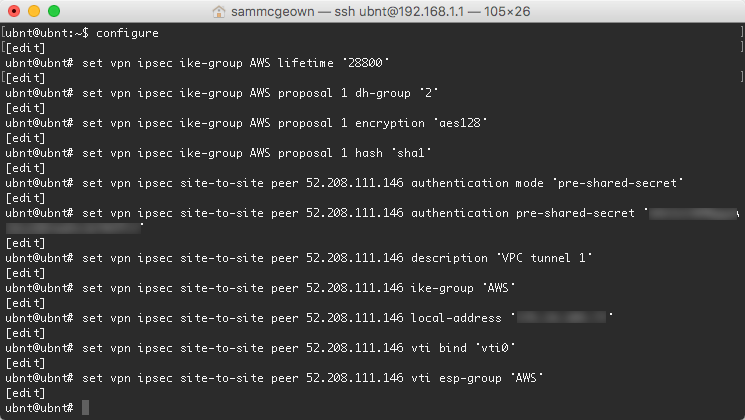
Commit and save your new configuration
commit save
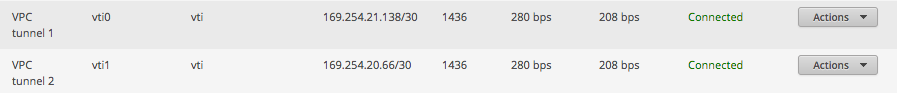
The VPN connection should now come up, to verify this I logged onto my EdgeMax dashboard and could see the new VPC tunnel connections were indeed connected:
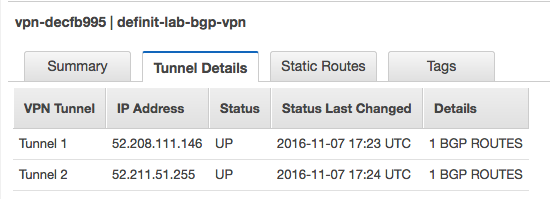
Logging on to my VPC console, I can see that the VPN connection’s tunnel details are also up.
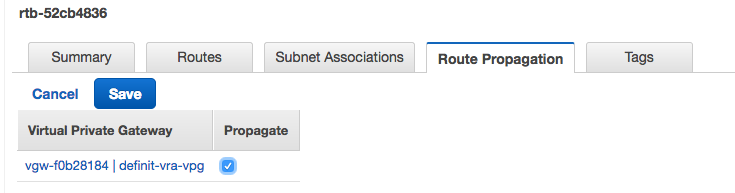
Enable route propagation
The final step is to enable route propagation on the Route Tables tab in the VPC dashboard. Select the route table and then select the Route Propagation tab, click Edit and then check the Propagate box:
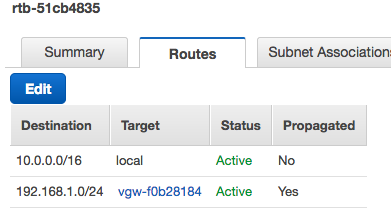
In a second or two, the subnet behind the EdgeRouter should be in the Routes table:
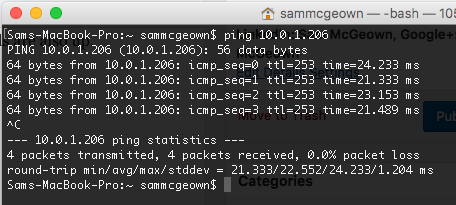
Testing Connectivity
Now when I spin up a new EC2 instance in the DefinIT-vRA VPC, I can configure the Security Group to allow ICMP and SSH from my local subnet
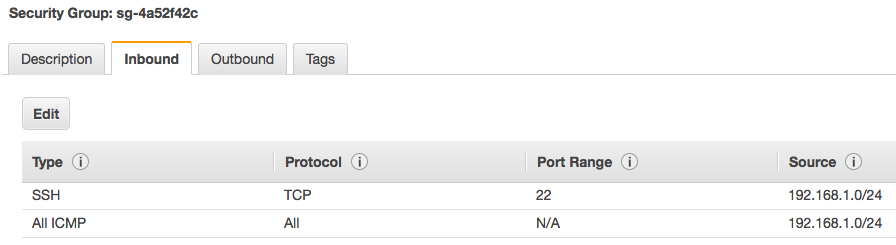
And testing I can ping and SSH to the instance.