Using PowerShell to add IP addresses to IIS7’s FTP IPv4 Address and Domain Restrictions
 Today I was configuring a new FTP server based on IIS7 (well, 7.5 technically as it’s a Server 2008 R2 host), and I wanted an easy way to add and remove allowed IP addresses based on either an XML config file or a CSV import. Customers’ IP addresses are added or removed regularly, but I didn’t want to have to update their details twice, once on the server and once in the documents.
Today I was configuring a new FTP server based on IIS7 (well, 7.5 technically as it’s a Server 2008 R2 host), and I wanted an easy way to add and remove allowed IP addresses based on either an XML config file or a CSV import. Customers’ IP addresses are added or removed regularly, but I didn’t want to have to update their details twice, once on the server and once in the documents.
I figured that the PowerShell extensions for managing IIS would do nicely – they are great for managing IIS sites after all and the idea with FTP in IIS7 is that it doesn’t care which protocol you are using, HTTP, HTTPS, FTP or FTP over SSL – all should be configured the same way.
The security setup had to follow the policy that all IP addresses are denied unless explicitly allowed.
I imported the module and listed the cmdlets:
Import-Module –Name WebAdministration
Get-Command –PSSnapin WebAdministration
Creating a new FTP site
This is very, very simple with PowerShell
New-WebFtpSite -Name ‘FTP Site’ -IPAddress ‘192.168.10.22’ -HostHeader ‘ftp.mcgeown.co.uk’ -PhysicalPath ’d:\FTP\
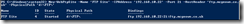
A good start then!
By default, the site will allow any IP address to access the server – it’s time to start locking it down.
Allow Authorised Users
- Add-WebConfiguration -Filter /system.ftpserver/security/authorization -PSPath ‘IIS:' -Value @{accessType=‘Allow’;users=’*’;permissions=3} -Location ‘FTP Site’
Restricting IP Access
Unfortunately the IP Address Restrictions part of the configuration isn’t exposed directly by a cmdlet so I thought I’d use one or two of the lower level IIS configuration cmdlets – Add-WebConfiguration, and Set-WebConfigurationProperty. And after a lot of fiddling and a lot of help by a colleague, I stumbled upon the correct syntax:
Set-WebConfigurationProperty -Filter /system.ftpserver/security/ipsecurity -Name allowUnlisted -Value $false -Location ‘FTP Site’ -PSPath ‘IIS:'
Add-WebConfiguration -Filter /system.ftpserver/security/ipsecurity -PSPath ‘IIS:' -Value @{ipAddress=’192.168.1.1’;subnetMask=’255.255.255.255’;allowed=$true} –Location ‘FTP Site’
The following code is appended to the end of the applicationHost.config file – now hopefully you can see that the crazy colours relate to the section in the same colour on below:
«span style=“color: #ff00ff”>location path=“FTP Site” >
«span style=“color: #004000”>system.ftpServer>
«span style=“color: #008000”>security>
«span style=“color: #00ff00”>ipSecurity allowUnlisted=“false”>
«span style=“color: #ff8000”>add ipAddress=“192.168.1.1” allowed=“true” />
</ipSecurity>
«span style=“color: #80ff00”>authorization>
«span style=“color: #8000ff”>add accessType=“Allow” users="*" permissions=“Read, Write” />
</authorization>
</security>
</system.ftpServer>
</location>
Scripting the whole thing
I’ve created two files, Add-AllowedIPs.ps1 and AllowedIPs.config. The config file is just an XML structure with the allowed IPs and Site name:
192.168.8.1 255.255.255.255 10.10.10.0 255.255.254.0
The ps1 file is a simple script to read the configuration and apply the settings:
$ConfigFile= “AllowedIPs.config”
if(Test-Path $ConfigFile){[xml]$Config = Get-Content $ConfigFile}else{throw (“Unable to find configuration file: " + $ConfigFile)}$Site = $Config.Configuration.Site.Name
Write-Host “Clearing $Site IP Security Lists” -BackgroundColor Yellow -ForegroundColor DarkBlue
Clear-WebConfiguration -Filter /system.ftpserver/security/ipsecurity -PSPath ‘IIS:' -Location “$Site”
Write-Host “Adding Allowed IPs to $Site” -BackgroundColor Yellow -ForegroundColor DarkBlue
$Config.Configuration.Site.Address | foreach {
$IP = $.IP.Trim()
$SubnetMask = $.SubnetMask.Trim()
Add-WebConfiguration -Filter /system.ftpserver/security/ipsecurity -PSPath ‘IIS:' -Location “$Site” -Value @{ipAddress="$IP”;subnetMask="$SubnetMask";allowed=$true}
}
Not quite sure why doing something so simple should have occupied so much of my time, but I hope it saves you some!
Sam

