Security “fun” and embracing 2FA
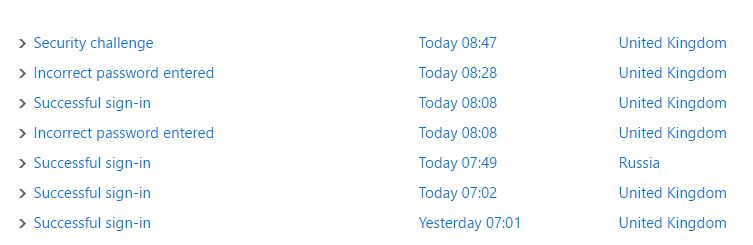
 So the other day my Skype account was briefly compromised, a successful login from Russia (after digging through activity logs) and this was after many attempts from IP addresses all around the world (China, Korea, Argentina the list goes on). You can see from the picture below the successful login attempt.
So the other day my Skype account was briefly compromised, a successful login from Russia (after digging through activity logs) and this was after many attempts from IP addresses all around the world (China, Korea, Argentina the list goes on). You can see from the picture below the successful login attempt.
My initial reaction was stress and panic, as I didn’t know precisely where I had been compromised I ran scans on my local machines while resetting passwords a plenty. Once I had calmed down a bit and reviewed where I had gone wrong I set about uping my game.
You see I had been using what I considered reasonably secure 8 character(or longer) alpha numeric passwords (also avoiding to use the same password on any accounts) so I felt pretty secure.
What I discovered and purely my own fault was one of my old passwords was not inline with above but was still active (but not used) so it was indeed the weakest link.
My guess at this point is that after numerous brute force attempts (which I could see in the activity logs) mister hacker and his bots managed to get one successful login to my Skype account and briefly spam people (interestingly not all the contacts in Skype were sent a nasty link)
I was already using 2 Factor Authentication for a few things but after the incident I went all in.
It took a little while to get everything that I wanted locked down and enabled for 2FA but all of the products I use seemed to support either 3rd party 2FA or have a suitable offering themselves.
Setting it up was a pain for a few things as some of the documentation was not so easy to find and frankly some applications do not cope so well with 2FA.
A couple of the 2FA offerings I am using now which work very well.
- Microsoft 2 Factor Authentication
- Google Authenticator
In short this was a lesson learned, I was complacent (with just one password) but it was clearly enough therefore for me, it doesn’t matter how small your weakest link is in your personal security is it can and will get exploited if left long enough.

