NSX
 Written by Sam McGeown
on 12/6/2019
Written by Sam McGeown
on 12/6/2019
I’ve done a fair amount of work learning VMware PKS and NSX-T, but I wanted to drop down a level and get more familiar with the inner workings for Kubernetes, as well as explore some of the newer features that are exposed by the NSX Container Plugin that are not yet in the PKS integrations.
The NSX-T docs are…not great, I certainly don’t think you can work out the steps
required from the official
 Written by Sam McGeown
on 23/5/2019
Written by Sam McGeown
on 23/5/2019
I ran into this UI bug the other day when I was trying to enable route redistribution on an Edge in a Secondary site of a cross-vCenter NSX deployment.
The Edge itself was deployed correctly, and configured to peer with a physical northbound router, however when I attempted to configure the route redistribution I was unable to do so.
Fortunately, the solution was simple - use the API.
 Written by Sam McGeown
on 29/6/2018
Written by Sam McGeown
on 29/6/2018
Yesterday, Pivotal Container Service 1.1 dropped and, as it’s something I’ve been actively learning in my lab, I wanted to jump on the upgrade straight away. PKS with NSX-T is a really hot topic right now and I think it’s going to be a big part of the future CNA landscape.
My Lab PKS 1.0.4 deployment is configured as a “NO-NAT with Logical Switch (NSX-T) Topology” as depicted in the diagram below (from the PKS documentation). My setup has these network characteristics:
 Written by Sam McGeown
on 26/3/2018
Written by Sam McGeown
on 26/3/2018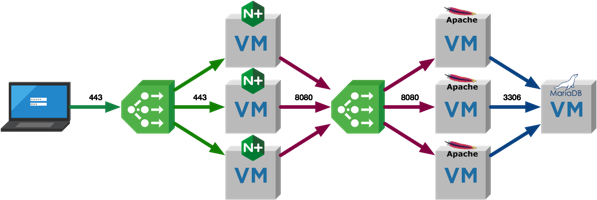
One question I’m asked quite a lot is what I use for a 3-tier application when I’m testing things like NSX micro-segmentation with vRealize Automation. The simple answer is that I used to make something up as I went along, deploying components by hand and generally repeating myself a lot. I had some cut/paste commands in my note application that sped things up a little, but nothing that developed. I’ve been meaning to rectify this for a while, and this is the result!
 Written by Sam McGeown
on 26/1/2018
Written by Sam McGeown
on 26/1/2018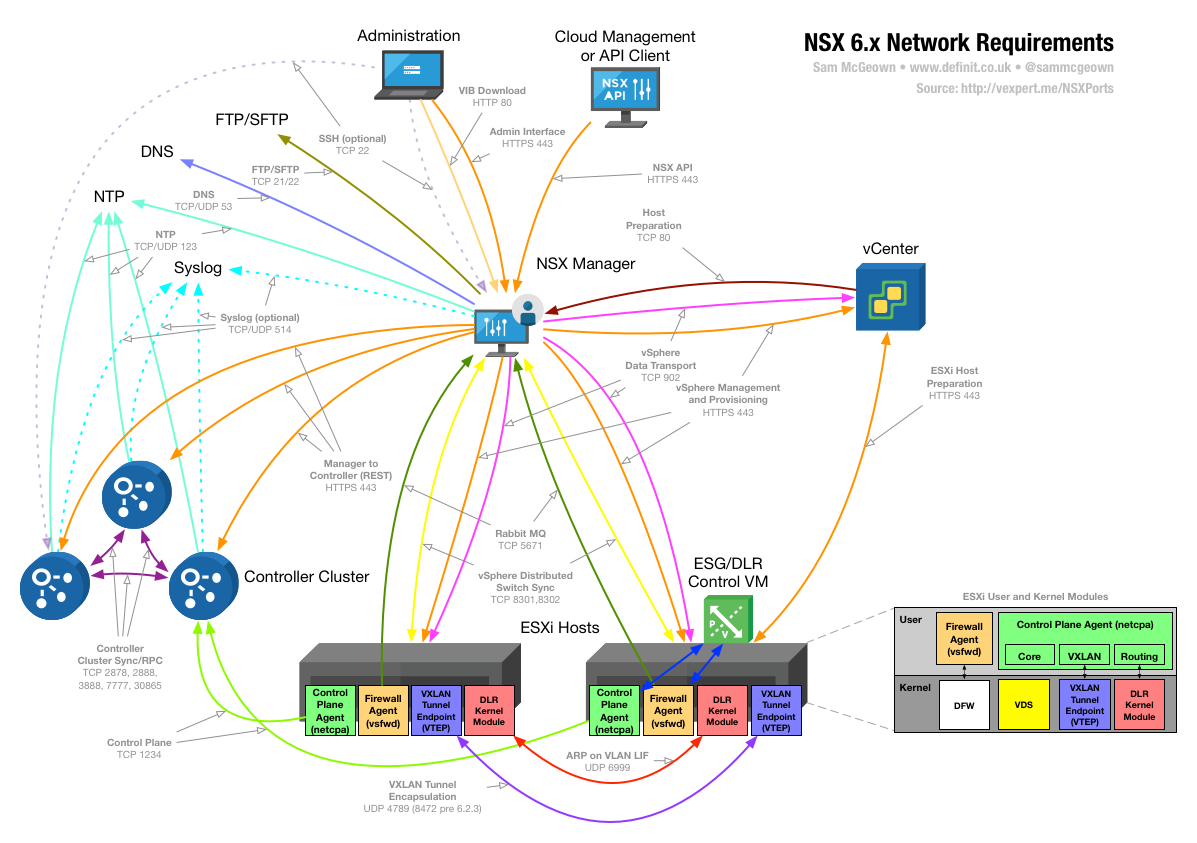
There are a few NSX Communications network diagrams floating around, but none have really displayed the info in a way I found to be clear or complete enough. To that end, I have been working on a diagram that covers as much of the communications between NSX Components as I can. I’ve currently only covered single site NSX (not Cross vCenter) but I’ll publish an updated version soon including that.
 Written by Sam McGeown
on 19/1/2018
Written by Sam McGeown
on 19/1/2018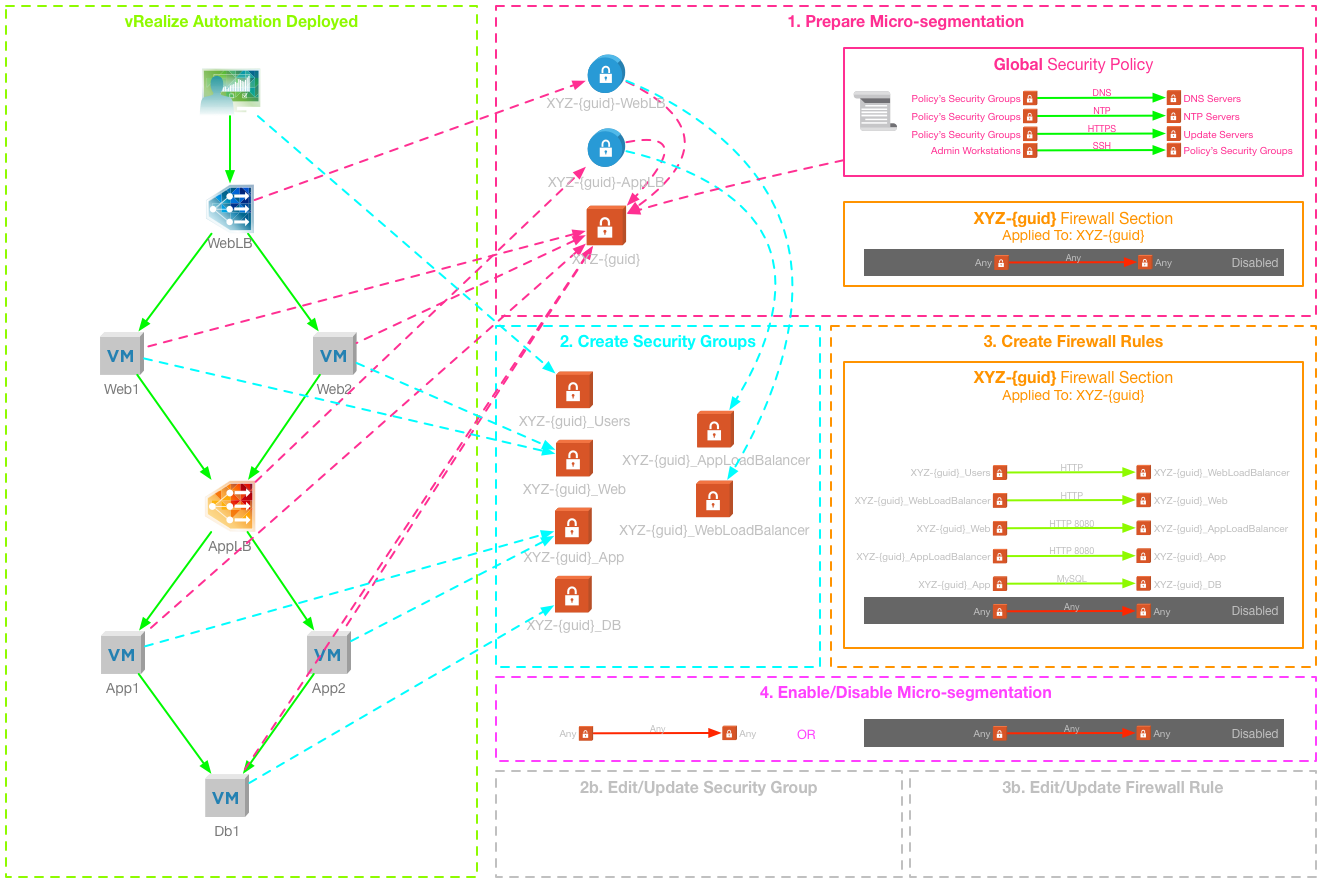
 vRealize Automation and NSX integration has introduced the ability to deploy multi-tiered applications with network services included. The current integration also enables a method to deploy micro-segmentation out of the box, based on dynamic Security Group membership and the Service Composer. This method does have some limitations, and can be inflexible for the on-going management of deployed applications. It requires in-depth knowledge and understanding of NSX and the Distributed Firewall, as well as access to the Networking and Security manager that is hosted by vCenter Server.
vRealize Automation and NSX integration has introduced the ability to deploy multi-tiered applications with network services included. The current integration also enables a method to deploy micro-segmentation out of the box, based on dynamic Security Group membership and the Service Composer. This method does have some limitations, and can be inflexible for the on-going management of deployed applications. It requires in-depth knowledge and understanding of NSX and the Distributed Firewall, as well as access to the Networking and Security manager that is hosted by vCenter Server.
 Written by Sam McGeown
on 22/12/2017
Written by Sam McGeown
on 22/12/2017
Yesterday saw the release of NSX-T 2.1, with some new features and also some usability enhancements. You can check out the release notes here
As I’m mid-way through this blog series, I thought I’d stick in the upgrade as a little bonus!
Download the upgrade bundle

Validate the version and status of NSX-T components
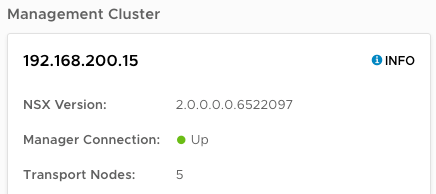
Check the Controller cluster status and Manager connections are up.
 Written by Sam McGeown
on 19/12/2017
Written by Sam McGeown
on 19/12/2017Disclaimer! I am learning NSX-T, part of my learning is to deploy in my lab - if I contradict the official docs then go with the docs!
Lab Environment
This NSX-T lab environment is built as a nested lab on my physical hosts. There are four physical ESXi hosts, onto which I will deploy three ESXi VMs, a vCenter Server Appliance, NSX Manager, an NSX Controller cluster, and two NSX Edge Nodes.
 Written by Sam McGeown
on 23/10/2017
Written by Sam McGeown
on 23/10/2017
Disclaimer! I am learning NSX-T, part of my learning is to deploy in my lab - if I contradict the official docs then go with the docs!
Lab Environment
This NSX-T lab environment is built as a nested lab on my physical hosts. There are four physical ESXi hosts, onto which I will deploy three ESXi VMs, a vCenter Server Appliance, NSX Manager, an NSX Controller cluster, and two NSX Edge Nodes.
 Written by Sam McGeown
on 23/10/2017
Written by Sam McGeown
on 23/10/2017Disclaimer! I am learning NSX-T, part of my learning is to deploy in my lab - if I contradict the official docs then go with the docs!
Lab Environment
This NSX-T lab environment is built as a nested lab on my physical hosts. There are four physical ESXi hosts, onto which I will deploy three ESXi VMs, a vCenter Server Appliance, NSX Manager, an NSX Controller cluster, and two NSX Edge Nodes.

