Secure
 Written by Simon Eady
on 8/3/2016
Written by Simon Eady
on 8/3/2016Those of you used to using vSphere on a regular basis will already be aware of the hardening guide for ESXi and vSphere but what about vROps?
If the vROps appliance needs to be hardened there is already a VMware provided guide and tool to accommodate.
Secure configuration guide -
“The documentation for Secure Configuration is intended to serve as a secure baseline for the deployment of vRealize Operations Manager.”
 Written by Sam McGeown
on 6/1/2015
Written by Sam McGeown
on 6/1/2015
It’s a fairly common requirement when creating a new user to assign a randomly generated password, so during a recent engagement I wrote a little password generator to do that. I wanted to be able to chose whether special characters were used, and the length of the password - typically if the password doesn’t used special characters I would increase the length significantly!
Characters should be randomly picked from:
- a-z
- A-Z
- 0-9
- (optional) ASCII special characters
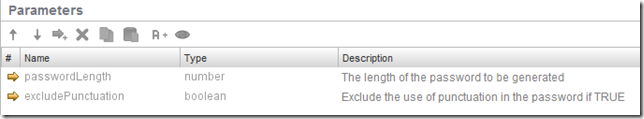
Inputs
- passwordLength - the length of the password to be generated (number)
- excludePunctuation - exclude the use of special characters if TRUE (boolean)
 Written by Sam McGeown
on 29/6/2011
Written by Sam McGeown
on 29/6/2011It’s a fairly common requirement – setting up a guest WiFi network that is secure from the rest of your LAN. You need a secure WLAN access for the domain laptops which has full access to the Server and Client VLANs, but you also need a guest WLAN for visitors to the office which only allows internet access. Since the budget is limited, this must all be accomplished via a single Access Point – for this article, the access point is a Cisco WAP4410N.
