Security
 Written by Simon Eady
on 2/11/2016
Written by Simon Eady
on 2/11/2016 So the other day my Skype account was briefly compromised, a successful login from Russia (after digging through activity logs) and this was after many attempts from IP addresses all around the world (China, Korea, Argentina the list goes on). You can see from the picture below the successful login attempt.
So the other day my Skype account was briefly compromised, a successful login from Russia (after digging through activity logs) and this was after many attempts from IP addresses all around the world (China, Korea, Argentina the list goes on). You can see from the picture below the successful login attempt.
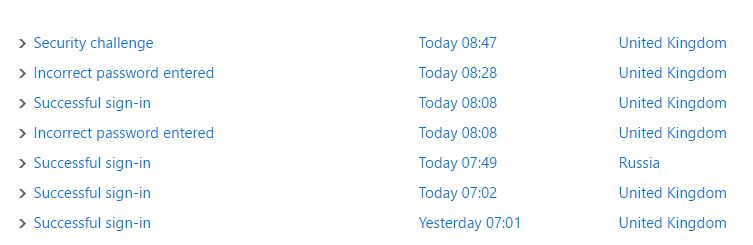
My initial reaction was stress and panic, as I didn’t know precisely where I had been compromised I ran scans on my local machines while resetting passwords a plenty. Once I had calmed down a bit and reviewed where I had gone wrong I set about uping my game.
 Written by Simon Eady
on 8/3/2016
Written by Simon Eady
on 8/3/2016Those of you used to using vSphere on a regular basis will already be aware of the hardening guide for ESXi and vSphere but what about vROps?
If the vROps appliance needs to be hardened there is already a VMware provided guide and tool to accommodate.
Secure configuration guide -
“The documentation for Secure Configuration is intended to serve as a secure baseline for the deployment of vRealize Operations Manager.”
 Written by Sam McGeown
on 11/2/2015
Written by Sam McGeown
on 11/2/2015vRealize Log Insight 2.5 improves on the clustering in previous versions with an Integrated Load Balancer (ILB) which allows you to distribute load across your cluster of Log Insight instances without actually needing an external load balancer. The advantage of this over an external load balancer is that the source IP is maintained which allows for easier analysis.
The minimum number of nodes in a cluster is three, the first node becomes the Master node and the other two become Worker nodes. The maximum number of nodes supported is six, though acording to Mr Log Insight himself,
 Written by Sam McGeown
on 15/10/2014
Written by Sam McGeown
on 15/10/2014
It is with great relief that I can announce I have passed my VCP NV (Network Virtualisation) having been caught out by the difficulty of the exam and failing previously.
Exam Preparation
I was fortunate to attend a VMware internal bootcamp (roughly equivalent to the ICM course) for NSX and have had experience deploying production NSX environments, so that is by far the best preparation. As always, the
 Written by Sam McGeown
on 11/9/2014
Written by Sam McGeown
on 11/9/2014The NSX Edge Gateway comes pre-armed with the ability to provide an SSL VPN for remote access into your network. This isn’t a new feature (SSL VPN was available in vCloud Networking and Security), but it’s worth a run through. I’m configuring remote access to my Lab, since it’s often useful to access it when on a client site, but traditional VPN connections are often blocked on corporate networks where HTTPS isn’t.
 Written by Sam McGeown
on 23/6/2014
Written by Sam McGeown
on 23/6/2014This is the first article in a series about how to build-out a simple vCAC 6 installation to a distributed model.
In a simple installation you have the Identity Appliance, the vCAC appliance (which includes a vPostgres DB and vCenter Orchestrator instance) and an IaaS server. The distributed model still has a single Identity Appliance but clusters 2 or more vCAC appliances behind a load balancer, backed by a separate vPostgres database appliance. The IaaS components are installed on 2 or more IaaS Windows servers and are load balanced, backed by an external MSSQL database. Additionally, the vCenter Orchestrator appliance is used in a failover cluster, backed by the external vPostgres database appliance.
 Written by Sam McGeown
on 20/3/2014
Written by Sam McGeown
on 20/3/2014In my previous post
 Written by Sam McGeown
on 13/3/2014
Written by Sam McGeown
on 13/3/2014As a little learning project, I thought I’d take on
 Written by Sam McGeown
on 5/3/2014
Written by Sam McGeown
on 5/3/2014I’m fairly new to SRM, but even so this one seemed like a real head-scratcher! If you happen to be using CA signed certificates on your “protected site” vCenter and “recovery site” vCenter servers, when you come to linking the two SRM sites you encounter SSLHandShake errors – basically SRM assumes you want to use certificates for authentication because you’re using signed certificates. If you use the default self-signed certificates, SRM will default to using password authentication (see SRM Authentication). Where the process fails is during the “configure connection” stage, if either one of your vCenter servers does not have CA signed and the other does (throws an error that they are using different authentication methods) or that you are using self-signed certificates for either SRM installation (throws an error that the certificate or CA could not be trusted).
 Written by Sam McGeown
on 6/11/2013
Written by Sam McGeown
on 6/11/2013In my post yesterday (vexpert.me/hS) I talked about how to recover from an expired default SSO administrator password – this prompted a discussion on twitter with Anthony Spiteri (@anthonyspiteri) and Grant Orchard (@grantorchard) about the defaults for expiration and how to mitigate the risk.
The first solution is to modify the password expiration policy for SSO. I’m not advocating this necessarily – I think that expiring passwords ensure that you change them regularly and increase the overall security of your SSO solution. However, I can envisage situations (similar to mine) when the SSO administrator account is not used for a long time and expired – that causes headaches.
