Sso
 Written by Sam McGeown
on 12/9/2014
Written by Sam McGeown
on 12/9/2014SSO is a fundamental requirement when deploying vCAC, whether for a distributed or simple installation. This walk through goes through the deployment and configuration of the vCAC Identity Appliance, which provides a stand alone SSO instance for vCAC.
Some of the posts in this series are completed with vCAC 6.0.1, others will be with 6.1. Where there are differences I will aim to point them out!
 Written by Sam McGeown
on 6/11/2013
Written by Sam McGeown
on 6/11/2013In my post yesterday (vexpert.me/hS) I talked about how to recover from an expired default SSO administrator password – this prompted a discussion on twitter with Anthony Spiteri (@anthonyspiteri) and Grant Orchard (@grantorchard) about the defaults for expiration and how to mitigate the risk.
The first solution is to modify the password expiration policy for SSO. I’m not advocating this necessarily – I think that expiring passwords ensure that you change them regularly and increase the overall security of your SSO solution. However, I can envisage situations (similar to mine) when the SSO administrator account is not used for a long time and expired – that causes headaches.
 Written by Sam McGeown
on 5/7/2013
Written by Sam McGeown
on 5/7/2013 Yesterday I attended my second ever #LonVMUG and did my first ever VMUG presentation! Generally it was a great day, with loads of really good sessions and some really cool community and vendor content.
Yesterday I attended my second ever #LonVMUG and did my first ever VMUG presentation! Generally it was a great day, with loads of really good sessions and some really cool community and vendor content.
As ever it was great day for socialising and networking with people who you interact with on twitter. For me one of the major benefits of the VMUG is learning from other people’s experience. Twitter was alive with the hastag #LonVMUG and it definitely adds something to the day to be active
 Written by Sam McGeown
on 15/2/2013
Written by Sam McGeown
on 15/2/2013This article originally started off life as a record of how I managed to get this working, as a lot of my posts do, but this time it appears I am foiled.
Last week, I had 3 vCenter Servers that appeared to be happily talking to each other in Linked Mode sharing a singe Multi-site SSO domain without any real issues. I had a single-pane-of-glass view of all 3 and I could manage them all from the one client. The reason for the 3 vCenter servers was segregation of LAN and DMZ networks: vCenter001 was in the LAN, vCenter002 sat in DMZ1 and vCenter003 sat in DMZ2.
 Written by Sam McGeown
on 24/11/2012
Written by Sam McGeown
on 24/11/2012 While adding an additional vCenter Server to our Multi-Site Single Sign On instance I encountered a problem as I entered the details of the existing SSO.
While adding an additional vCenter Server to our Multi-Site Single Sign On instance I encountered a problem as I entered the details of the existing SSO.

The error thrown was:
User credentials are incorrect or empty. Provide correct credentials.
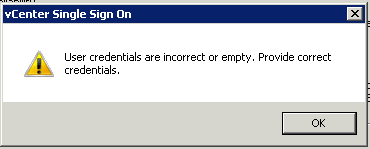
After a couple of hours online with VMware support I took a guess at the problem. On the existing Single Sign On Configuration I have added the Active Directory domain DefinIT and in order to enable integrated authentication from the vSphere Client I moved it to the top of the list - this meant that System-Domain is no longer the default authentication domain. The SSO admin account (admin@System-Domain) is a part of that domain and so my guess is that the installer tries to authenticate using [email protected] rather than System-Domain, which of course failed.
 Written by Sam McGeown
on 28/10/2012
Written by Sam McGeown
on 28/10/2012 VMware vSphere Single Sign On (SSO) can be installed in Multi-site mode to support local sign-on to vCenters that you want to be part of the same single sign on domain - for example, if you want to install Linked-Mode and have the advantage of a single pane of glass view, but can’t risk using a single SSO instance across the WAN. In other words, from
VMware vSphere Single Sign On (SSO) can be installed in Multi-site mode to support local sign-on to vCenters that you want to be part of the same single sign on domain - for example, if you want to install Linked-Mode and have the advantage of a single pane of glass view, but can’t risk using a single SSO instance across the WAN. In other words, from
